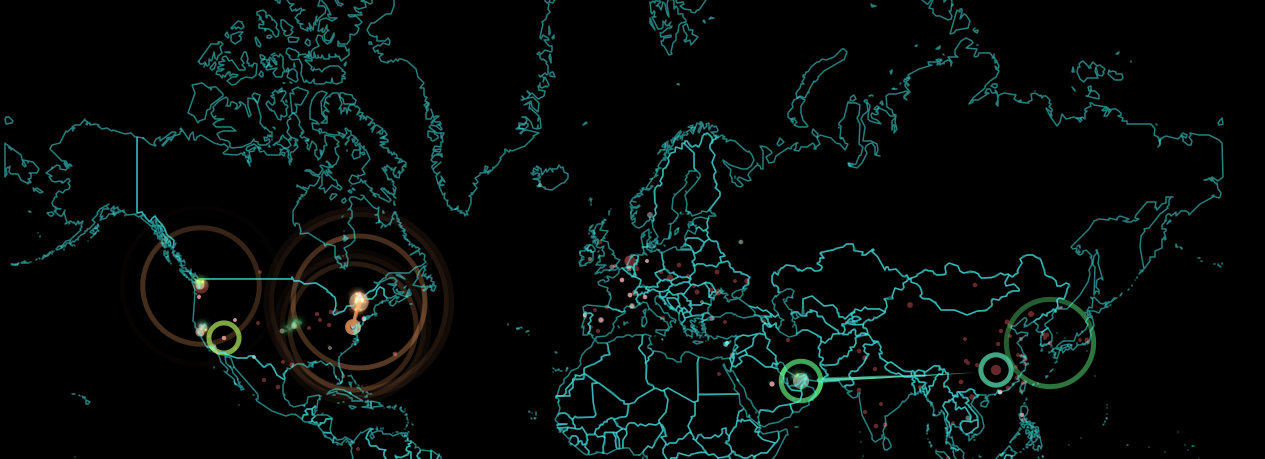
Q & A WITH XIE XUPING (SHIUHPYNG WINSTON SHIEH): CAN COMPUTER MODELS PREDICT MALWARE BEHAVIOR?
/台湾国立交通大学谢续平教授应邀来我院学术讲座
Date of Publication: 03.09.17. March 09, 2017/ 发布于:2017-03-09
Editor & Translator: Rosie YU Rizhen/ 编译:余日臻
Taiwan National Chiao Tung University, Professor Xie was invited to the Department of Cyberspace Security CSEE as a special guest for three days. One of the event was the “Auto-Constructing Malware Behavior Profilers” report at Hunan University CSEE Room 542.

The report meeting was chaired by Professor PENG Fei, director of the Department of Cyberspace Security, and hosted by Professor HU Yupeng. The main direction of Professor Xie academic curriculum, discipline development plan and related research were discussed. Xie encourages open discussion all the way during the whole report. Teachers and cyberspace security department students are presented. They exchange and share their teaching experience at the seminar with Prof. Xie. Professor Xie also gives academic research plan of young teachers in the future. He would love to put forward more for detailed guidance and recommendations, and proposed many opinions of his own.
NCTU computing science professor XIE Xuping is on a mission to fight back against these lethal outbreaks using his weapon of choice: profilers.
Shiuhpyng Winston Shieh, an IEEE Fellow, ACM Distinguished Scientist, and Distinguished Professor of Chinese Institute of Electrical Engineers. Recently, He received IEEE Reliability Society Engineer of The Year Award and NCTU Distinguished Teaching Award. His research interests include system penetration and protection, malware behavior analysis, network and system security.
Rosie sat down at the report with professor Xie and other teachers to find out more about the evolution of computer viruses, the perils of logical key resistance, and profiler’s role in predicting threats.

What is your research focus?
I’m primarily interested in understanding the development of intuitive detection—everything from the internet virus attack and defense, all the way to prevent the spread of malware through popular operating systems.
A great deal of my expertise lies in constructing models—I build mathematical models and develop computational algorithms to look at virus, or how an threat unfolds over time. Ultimately, I’m looking for the best intervention to control these malwares, especially in low-resource settings where virus tend to spread rapidly.
How do you tackle threat problem?
First, I write down a model and then I see how closely the trends recapitulate the actual trends that we’ve observed in the past. By matching the past, we can have a reasonable idea of what the future is going to hold. That’s mostly at the population level. At the college level, a lot of the questions center on the emergence of changes of keys and, in particular, the changes that confer resistance to anti-virus software, which is a big public problem.
What’s the biggest challenge?
We’ve been trying to control these virus and malware with anti-virus software products, but now computer keys are developing resistance, in large part due to the secrecy of backward induction. And like we can see those changes in the genome, where genetic mutations lead to resistance.
Where are cyberspace attacks most common? Is globalization a trigger?
Virus are more prevalent in concentrated populations, but given that we have a globally connected world, we’re not just addressing this problem “over there,” it’s also potentially a threat everywhere.
I don’t think it’s right to think about it as a local problem in one particular region, because we’re basically becoming one big village.
At our University in Taiwan, we opened a college specifically to tackle Cyberspace malware problems which is called the Capture the Flag (CTF) College. The name is funny because we want to be the terminator of black hackers, so we chose the last zodiac animal of pig (Hai) and named it as the “Hai Ke Academy”.
Can we ever completely stop the spread? How would you describe the dynamic between humanity and hacker behaviors?
At the moment, we’re engaged in an arms race with these hackers. We’re making new profilers and the hackers are trying to find new ways to get around them. I think, ultimately, we need to find a different approach. I don’t know what it’s going to be, but I think some other approach will be necessary if we’re going to address the problem in a more sustainable way.
One of the ideas that’s been debated is, perhaps, instead of trying to eradicate the malware with auto-constructing malware behavior profilers, we could direct the evolution of these malware agents to be more benign, say more white side hackers to solve the problem. If we can never get rid of the flu, perhaps we can make it more like the common cold, instead of being an intense infection.
"That’s one of the big challenges in the field – how do we know when the next big threat is going to come?" Professor Xie uses computational modeling to track and predict the spread of computer virus.
What’s your role in Advanced Persistent Threat (APT) Challenge?
I see my role as helping to predict the outcomes of these different interventions. We don’t have a crystal ball, so the best we can do is understand what happened in the past, understand what’s happening now, and try to make the best guess at what’s going to happen in the future.
That’s what the computational methods that I’ve developed try to do. I write computer code to implement these ideas, and test them on real data.
Why do some viruses really manage to take hold, seemingly all of a sudden?
Much of it has to do with how well they are adapted to the Windows Operating System, some are to the Mac Operating System. To give an example of the virus: it was around for a while, but up until recently it didn’t seem to create any problems for your computer, but now we strongly suspect that it’s causing computer defects.
What I think is at play here is that the virus has adapted to the file (some in word documents, links or even PDFs) in a way that we couldn’t have predicted. It’s a very hard to predict which of the many viruses that we have today will be the next big threat.
We didn’t predict those famous attacks; they’re all surprises. That’s one of the big challenges in the field—how do we know when the next big threat is going to come?
Of course, from the point of view of the virus—and arguably this is what we all cares about—it is preventing advanced persistent threat (APT) passing on its control flow analysis code to the next generation. It must be somehow advantageous to the virus to be causing the thing that it’s causing in order to be able to reproduce further.
What are the pros to living in the age of big data?
I think we live at a time where the positive development is that we have more and more data on these keys and better and better ability to make sense of this data using the types of methods that my colleagues and I develop.
I do believe that in the long run new solutions are going to emerge from the collaboration of people like myself—who do the modeling and analysis—and computer scientist, engineers, public security authorities, ministries, governments, non-profits and maybe even software companies.
Contact Prof. Shieh at ssp@cs.nctu.edu.tw